Today's topic is on the core components of Amazon VPC & CloudWatch.
Tasks
1) Learn about the following to get started with VPC and post it on linkedIn:
Virtual private cloud (VPC)
VPC stands for Virtual Private Cloud.
Amazon Virtual Private Cloud (Amazon VPC) provides a logically isolated area of the AWS cloud where you can launch AWS resources in a virtual network that you define.
You have complete control over your virtual networking environment, including a selection of your IP address range, the creation of subnets, and configuration of route tables and network gateways.
You can easily customize the network configuration for your Amazon Virtual Private Cloud. For example, you can create a public-facing subnet for web servers that can access to the internet and can also place your backend system such as databases or application servers to a private-facing subnet.
You can provide multiple layers of security, including security groups and network access control lists, to help control access to Amazon EC2 instances in each subnet.
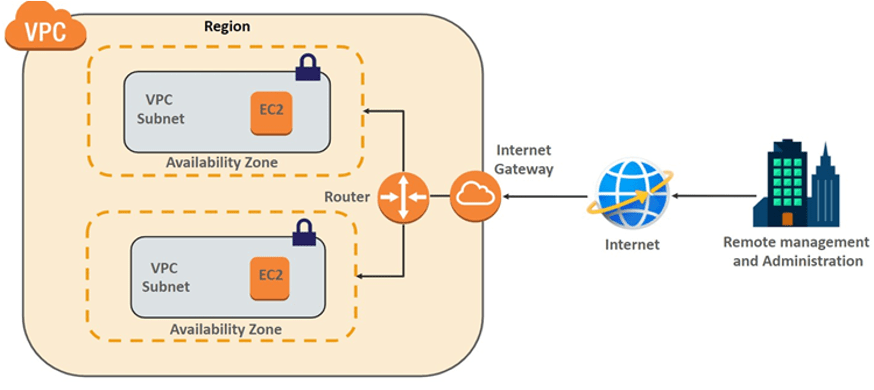
Subnets
A subnet is a range of IP addresses in your VPC. You launch AWS resources, such as Amazon EC2 instances, into your subnets. You can connect a subnet to the internet, other VPCs, and your own data centers, and route traffic to and from your subnets using route tables.
Internet Gateways
A gateway is a network node used in telecommunications that connects two networks with different transmission protocols together. Gateways serve as an entry and exit point for a network as all data must pass through or communicate with the gateway prior to being routed.
Route table
In AWS, a route table is a set of rules that determines where network traffic is directed. Each subnet in your AWS VPC is associated with a route table which controls the traffic flow between subnets.
Peering connections
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS Cloud. You can launch AWS resources, such as Amazon EC2 instances, into your VPC.
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. The VPCs can be in different Regions (also known as an inter-Region VPC peering connection).
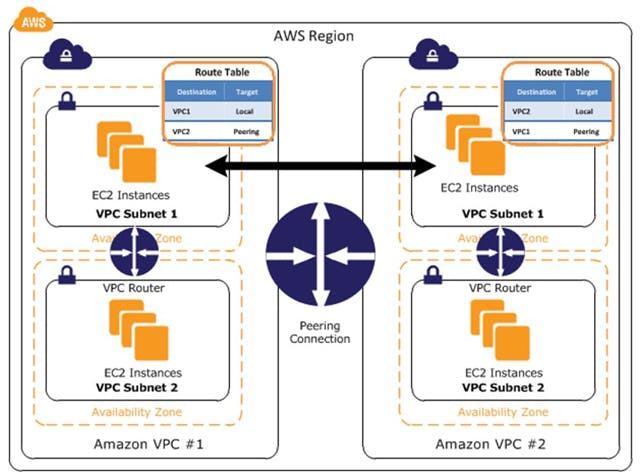
2) Imagine you're the cloud architect for a tech company, ByteConnect Inc. They've expanded rapidly, and each department operates in its own isolated cloud space (VPC). Now, the challenge is to establish a communication for their instances to communicate seamlessly using AWS Transit Gateway.
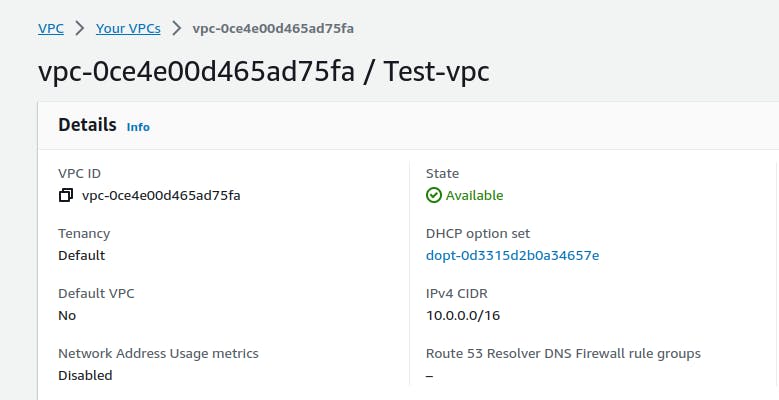
First create two VPC- Test VPC
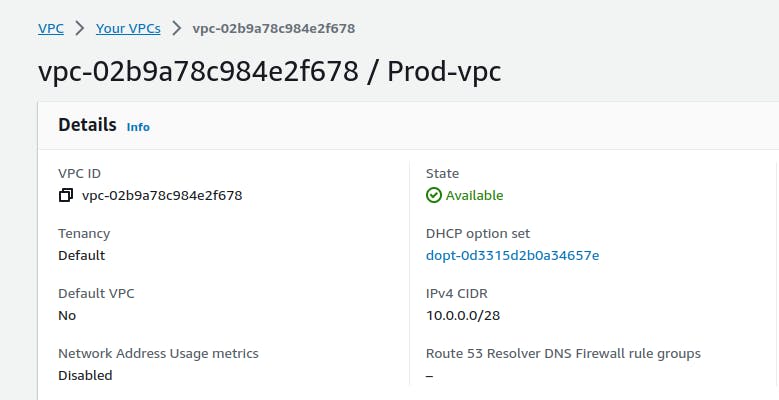
Second Prod VPC
Subnet for both created
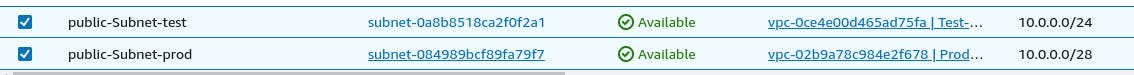
Route Table for both created
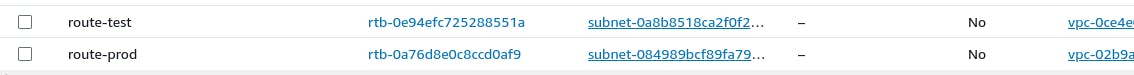
Internet Gateway for both created and attached

Two servers are created for both VPC

Now set connection - Peering Connection between both VPCs
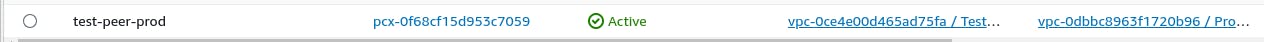
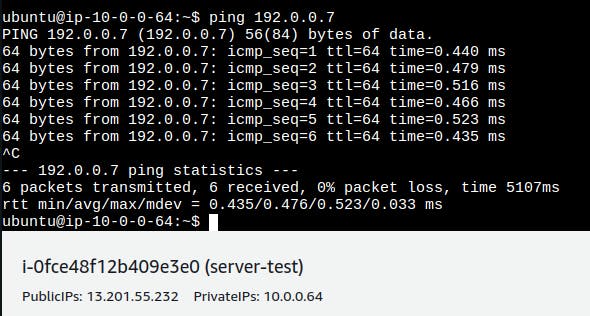
Now It's time to ping the Test Server by Prod Server
3) You are an AWS intern at XYZ company and you have to implement the concept of cloudwatch for your aws resource to monitor its logs.
What needs to be done:
Create an instance and deploy a nginx webserver on that instance.
Create a cloudwatch and connect it with your nginx server to monitor its logs.
Learn What is CloudWatch
CloudWatch enables you to monitor your complete stack (applications, infrastructure, network, and services) and use alarms, logs, and events data to take automated actions and reduce mean time to resolution (MTTR). This frees up important resources and allows you to focus on building applications and business value.
First let's create a EC2 instance
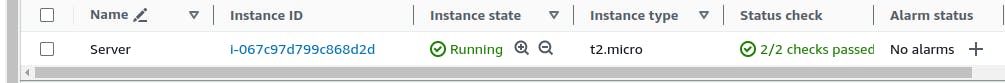
Install Nginx
# Update the system
sudo apt-get update
# Install Nginx
sudo apt-get install nginx
# To check wheather nginx has started or not
sudo systemctl start nginx
sudo systemctl status nginx
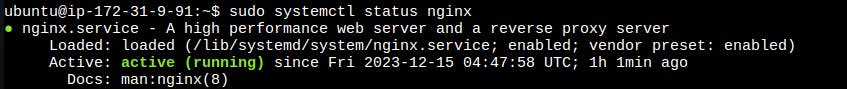
Set Up CloudWatch Logs for Nginx
sudo wget https://s3.amazonaws.com/amazoncloudwatch-agent/ubuntu/amd64/latest/amazon-cloudwatch-agent.deb
sudo dpkg -i -E ./amazon-cloudwatch-agent.deb
During the installation, configure it to collect and send logs to CloudWatch
sudo vim /opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.json
Example configuration:
{
"logs": {
"logs_collected": {
"files": {
"collect_list": [
{
"file_path": "/var/log/nginx/access.log",
"log_group_name": "NginxAccessLogs",
"log_stream_name": "{instance_id}"
},
{
"file_path": "/var/log/nginx/error.log",
"log_group_name": "NginxErrorLogs",
"log_stream_name": "{instance_id}"
}
]
}
}
}
}
Check CloudWatch Agent Status:
sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl -a status
If the agent is not running, start it.
sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl -a fetch-config -m ec2 -c file:/opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.json -s
Review Log Files:
Check the Nginx log files directly on your instance to make sure they are generating logs.
cat /var/log/nginx/access.log cat /var/log/nginx/error.logEnsure that the log files contain entries.
Check IAM Role Permissions:
- Verify that the IAM role associated with your EC2 instance has the necessary permissions to publish logs to CloudWatch. The role should have the policy
CloudWatchAgentServerPolicyattached.
- Verify that the IAM role associated with your EC2 instance has the necessary permissions to publish logs to CloudWatch. The role should have the policy
Security Group Rules:
- Ensure that the security group associated with your EC2 instance allows outbound traffic to the CloudWatch service.
Check CloudWatch Metrics:
- Navigate to the CloudWatch Metrics section and check if there are any metrics related to your EC2 instance and the logs you are monitoring. This can help identify if CloudWatch is receiving data.
Agent Log Files:
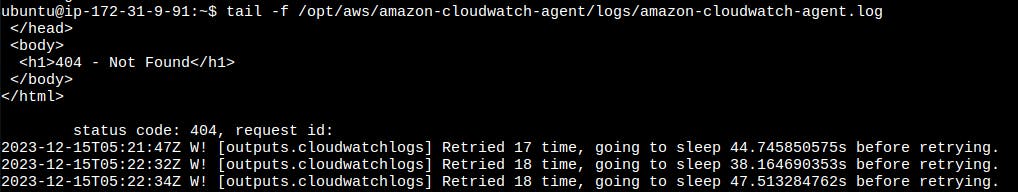
- Review the CloudWatch Agent logs for any errors or issues.
tail -f /opt/aws/amazon-cloudwatch-agent/logs/amazon-cloudwatch-agent.log
This command will show you the last few lines of the agent log in real-time.
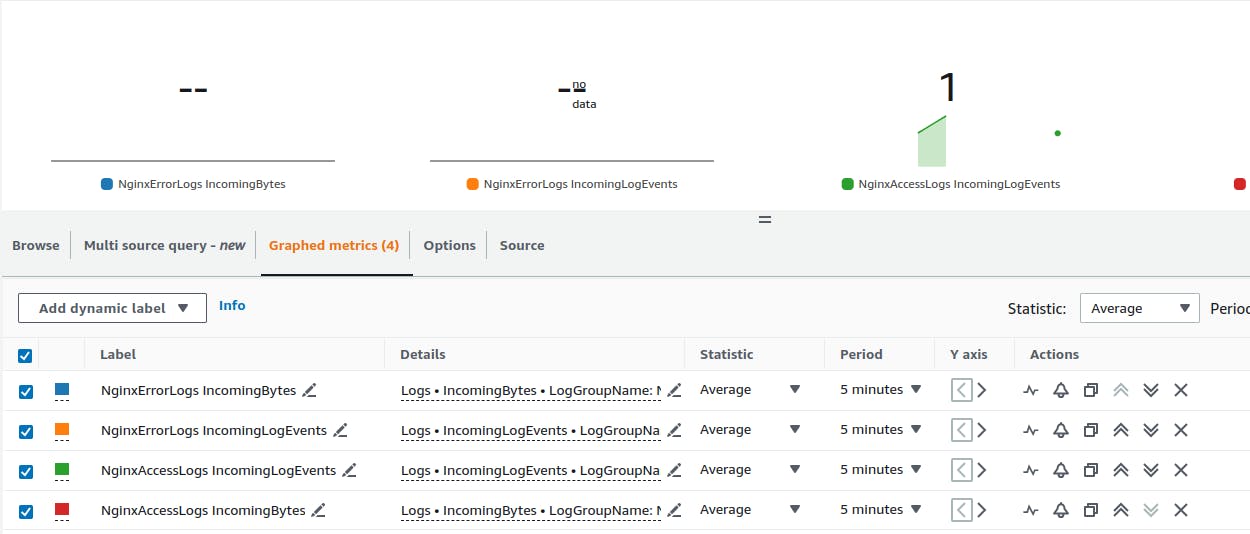
Here is the CloudWatch Log
DAY 5 Completed, Challenge taken from GitHub Repo.
Take the same, and you will enjoy this journey 😉
Feel free to explore more of my content, and don't hesitate to reach out if need any assistance from me or in case of you have any questions.
Happy Learning!
~kritika :)
